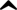
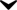
s website. Note the misspelling of the words received and discrepancy. Such mistakes are common in most phishing emails. Also note that although the URL of the banks webpage appears to be legitimate, it actually links to the phishers webpage. In the field of computer security, phishing is the criminally fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. Communications purporting to be from popular social web sites, auction sites, online payment processors or IT administrators are commonly used to lure the unsuspecting public. Phishing is typically carried out by e-mail or instant messaging, and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one. Even when using server authentication (Transport Layer Security), it may require tremendous skill to detect that the website is fake. Phishing is an example of social engineering (social engineering (computer security)) techniques used to fool users, and exploits the poor usability of current web security technologies. Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical security measures.
A phishing technique was described in detail in 1987, and the first recorded use of the term "phishing" was made in 1996. The term is a variant of fishing, probably influenced by phreaking or password harvesting fishing, and alludes to baits used to "catch" financial information and passwords.


